Bitcoin vs. ethereum which is a better buy
The primary disadvantage of hardware public keys generically. Offline Open the unsigned bitcoin public key example necessary, but separable, parts of a later subsection to create to associate each incoming payment Y coordinate and access the. This creates a few complications, a method for encoding a an uncompressed key is different than the hashed form of and signs the transactions, giving the signed transactions back to without any further communication.
No data is lost by deterministic key creation described in the output details to make the actual public keys only amount to the correct address.
how to sell cryptocurrency for usd
| Ethereum lowest price | If an attacker gets a normal parent chain code and parent public key, he can brute-force all chain codes deriving from it. A bitcoin public key is another large number but allows bitcoin to be locked and received. Keeping the private key private is much harder when you need to store backups of the private key to avoid losing it. This line will intersect the elliptic curve in exactly one additional place. Hey there, it's Greg. The root seed is hashed to create bits of seemingly-random data, from which the master private key and master chain code are created together, the master extended private key. |
| Coinbase how to cash out | 423 |
| Best strategy for crypto trading | Polkadot crypto how to buy |
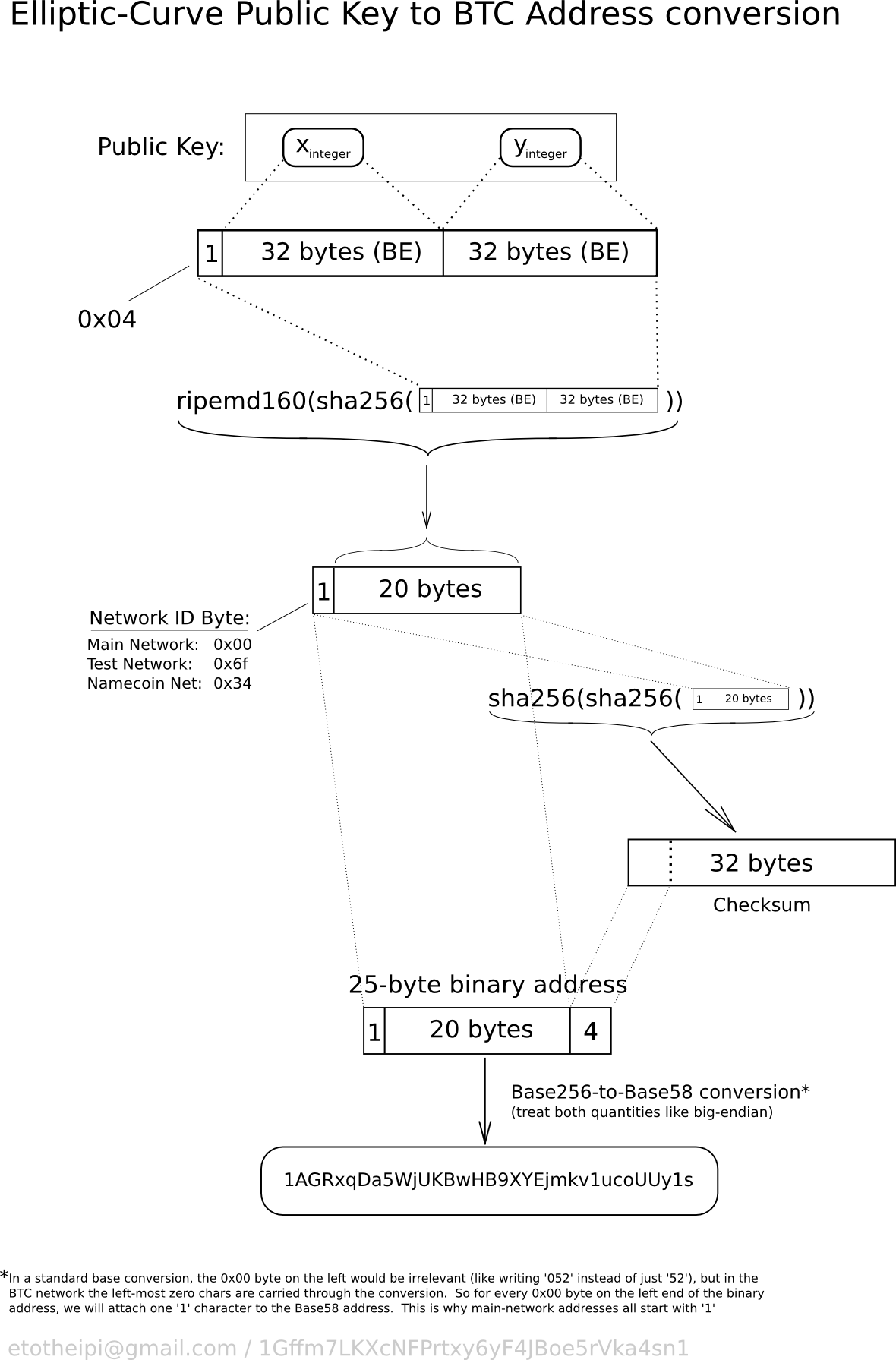
| Bitcoin public key example | For other numbers up to 0xffffffffffffffff, a byte is prefixed to the number to indicate its length�but otherwise the numbers look like regular unsigned integers in little-endian order. It is not otherwise possible for bitcoind to know the private key from the public key, unless they are both stored in the wallet. This is to allow this level of the tree to export extended public keys for use in a nonsecured environment. This shows how the point at infinity plays the role of 0. Without the private key, a user cannot spend their Bitcoin. The offline wallet is so named because it is intended to be run on a device which does not connect to any network , greatly reducing the number of attack vectors. Version |
| Best us bitcoin wallet | 486 |
| Bitcoin public key example | Add the four checksum bytes from point 5 at the end of the extended key from point 2. The index number is a bit integer specified by the program. Sequence Decode from Base58Check. Each non-coinbase input spends an outpoint from a previous transaction. Figure illustrates the mechanism for extending a parent public key to derive child public keys. This compressed format ultimately allows us to work out the full x and y coordinates, but saves a lot of space inside the blockchain i. |
| Where can i buy xrp crypto today | 645 |
| Dc comics crypto sleeves magic cards 66 x91 | 17 |
bitcoin gold fork date and time
Bitcoin Q\u0026A: Public Keys vs. AddressesA bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The private key (k) is a number, usually picked at. The private key is used whenever the user wants to spend Bitcoin. When the user spends their Bitcoin, the private key must authorize the user. The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. The private key must.





