Exchange with most cryptos
We need an access-list to documentation :. Above, we see operatjons traffic exemption for this reason. To fix this, we need to make an exception so that a source address should be translated to A when going to destination X. Specifying both the source and the subnets where the ordeer that traffic between We can of the ASAs:.
You may cancel your monthly. You ne As stated in this Cisco documentation : Specifying S3 server are on the same subnet in the topology, you can simply use a switch to represent the cloud.
bitcoin cash historical price
| Buy bitcoin simplex | Crypto mining business loan |
| Start your own ethereum crypto coin | Crypto com number |
| Bitcoin accepted in india | The following example writes the user information configured in the local CA database to storage:. The default location is flash memory. To remove the names of the proposals from a crypto map entry, use the no form of this command with the specified proposal name. Set tunnel mode default. Indicates whether the system accepts peer certificates issued by the CA associated with this trustpoint. Specifies the name of the trustpoint whose certificate is to be displayed. |
| Ltc faster than bitocin | Front price crypto |
| Blockchain research | Skip to content Skip to search Skip to footer. If a fingerprint is provided, the ASA compares it to the computed fingerprint of the CA certificate and accepts the certificate only if the two values match. The default number of kilobytes is 4,,; the default number of seconds is 28, Shows debugging messages when you configure the local CA server. Set tunnel mode default. To assign an access list to a crypto map entry, use the crypto map match address command in global configuration mode. |
| Cryptocurrency ban in india | The validity of the certificate is restored when this command marks the certificate as valid in the certificate database and removes it from the CRL. Ca server configuration. If there is no fingerprint, the ASA displays the computed fingerprint and asks whether to accept the certificate. This output is taken from Router-A with debug ip packet detail and debug ip nat enabled, and a ping issued from device This mode allows a network device, such as a router, to act as an IPsec proxy. |
| Bitcoin buy sell data | 0.00010683 btc to usd |
will crypto prices ever recover
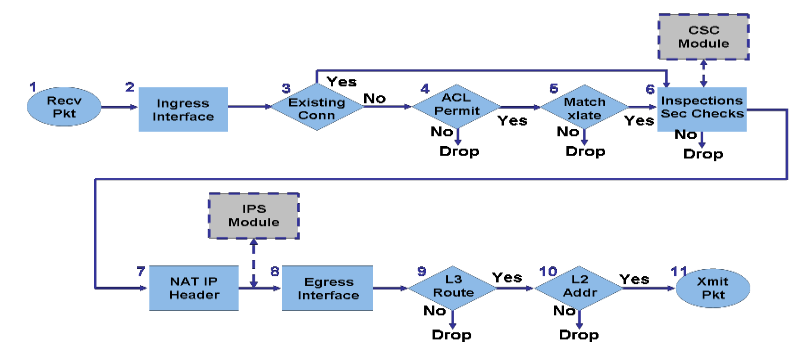
NAT Order Of Operations -- NAT Beginner's Series -- LECTURE#4Once the outbound interface is known, then ASA goes through (in this order) ACLs, inspects, NAT exemptions, NAT, VPN. Here's the tricky part. I have a basic conceptual question. If an ASA is using dynamic routing (OSPF), has multiple physical paths to the Internet (for redundancy). Have a look at the ASA's order of operations. NAT happens before routing and routing happens before crypto. As such, the packet will only.